04
Hashly — Generate Secure Hashes Instantly
Generate hashes instantly with Hashly. Create MD5, SHA-1, and SHA-256 checksums to verify files, track versions, and keep content consistent.
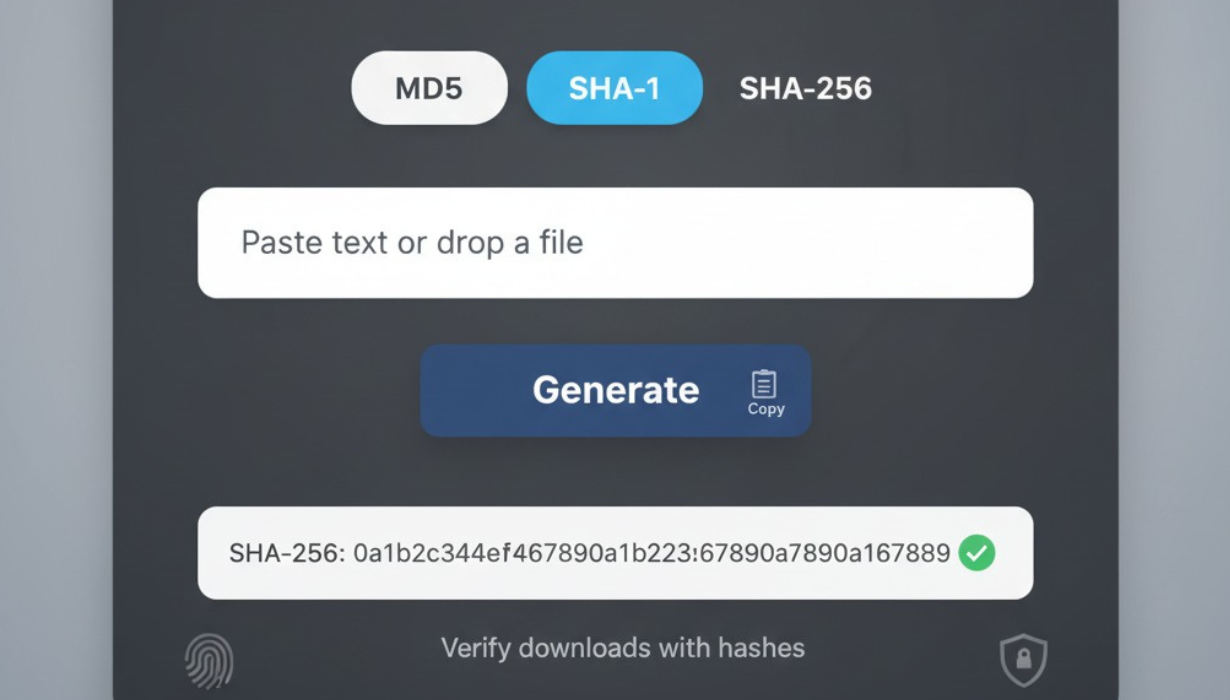
Hashly is the quick way to create dependable checksums on demand. Paste text or upload a file, choose your algorithm—MD5, SHA-1, or SHA-256—and Hashly returns a clean, copy-ready hash in seconds. If you publish downloads, keep shared assets in sync, or want a simple signal that a file hasn’t changed, Hashly turns “did this get altered?” into a one-click answer.
What Hashly Does (in plain language)
Hashes act like fingerprints for data. The same input will always produce the same fingerprint; change even a single character, and the fingerprint changes completely. Hashly gives you those fingerprints on demand so you can confirm that the item you’re sharing, storing, or reviewing is exactly the one you intended.
Why teams love using hashes
Reduce guesswork when handing off files between people and tools
Catch accidental edits before they cause confusion
Give readers a way to verify downloads and avoid corrupted transfers
Label large assets with short values that are easy to compare
Create a light audit trail for documentation, datasets, and releases
MD5 vs. SHA-1 vs. SHA-256 — which should you pick?
MD5 is fast and widely recognized. It’s fine for basic integrity checks in non-adversarial contexts (e.g., “did this upload finish correctly?”), but it’s not suitable where security matters.
SHA-1 is considered legacy for security-sensitive use because collisions have been demonstrated. Keep it for compatibility only.
SHA-256 is the modern default for checksums. It offers stronger collision resistance and broad support without adding unnecessary complexity.
Quick rule: use SHA-256 unless you have a specific reason not to.
Where Hashly helps the most
Content publishers add a checksum next to PDFs, ZIPs, and installers so readers can confirm authenticity.
Designers and producers include a hash in handoff notes to ensure the final file matches the approved version.
Technical writers and educators attach hashes to resources so students and editors can verify they downloaded the right item.
Ops teams keep reference hashes for configuration files to spot unintended changes after updates.
Researchers and analysts record hashes for datasets so collaborators know they’re working from the same source.
How to use Hashly in under a minute
Open Hashly and select your algorithm (SHA-256 is a great default)
Paste text or upload the file you want to check
Generate the hash and copy the result
Store the value next to the file—release notes, README, ticket, or spreadsheet—so it’s easy to verify later
Best practices for clean, reliable checksums
Always label the algorithm with the value (for example, “SHA-256: …”)
Keep the hash in the same place people find the file (download page, shared folder, or handoff doc)
Refresh the hash whenever you update the file—stale hashes create confusion
Use lowercase consistently and avoid line breaks in the value for easier comparison
If you publish for a broad audience, include a short note explaining how to compare the hash
What hashes can and can’t do
Hashes are perfect for integrity checks—confirming that content hasn’t changed. They are not passwords, keys, or encryption. If you need to protect stored credentials, use a slow, salted algorithm like bcrypt (see Bcryptor). If you need to keep contents private, use proper encryption. Hashly focuses on fast, dependable fingerprints, not secrecy.
Common mistakes (and easy fixes)
Relying on SHA-1 or MD5 when tampering is a concern → switch to SHA-256
Mixing algorithms within the same project → standardize on one and label values clearly
Forgetting to update the hash after edits → make “regenerate hash” part of your publish checklist
Treating a hash as a license or proof of authorship → it only proves the content hasn’t changed
Light SEO and accessibility tips for pages with hashes
Explain the purpose in one sentence above each value (“Use this SHA-256 to verify your download.”)
Use descriptive file names (brand-guidelines-v3.pdf) so people know what they’re verifying
Include alt text for any image that displays a hash and provide a selectable text version nearby
Team workflow ideas that stick
Add a “Checksum” line to release notes and changelogs
Keep a small “verification” section in your documentation template
Store a text file with the hash in the same folder as the asset
Teach new teammates to verify before sending or publishing
Include the hash and algorithm in tickets and pull requests so reviewers can confirm artifacts quickly
Practical examples you can copy today
Publishing a toolkit or dataset? Post “SHA-256:” and the value beneath the download link so users can compare locally.
Sharing design exports with a printer or stakeholder? Add a hash to the handoff note so everyone agrees on the exact file.
Maintaining internal scripts? Keep a reference hash in the repo to catch accidental edits during reviews.
Circulating classroom materials? Provide a hash so students can confirm they’ve downloaded the correct version.
Responsible use and data care
Only hash files you’re allowed to handle and share
Avoid exposing sensitive file names or paths when posting public checksums
Keep your storage, backups, and access controls strong—hashing is one layer, not a substitute for security
When in doubt about algorithm choice, prefer SHA-256 for long-term confidence
FAQs
Are hashes reversible?
No. They’re one-way fingerprints; you can’t reconstruct the original content from a hash.
Which algorithm should I use by default?
SHA-256. It’s broadly supported and collision-resistant for everyday integrity checks.
Is MD5 still useful?
It can be fine for quick, non-adversarial checks, but use SHA-256 where trust matters.
Can I use Hashly for passwords?
No. For passwords, use a slow, salted algorithm like bcrypt (our Bcryptor tool). Plain SHA or MD5 are not appropriate for password storage.
Why did my hash change after a tiny edit?
That’s expected—hashes are designed to change completely when the input changes even slightly.
Can I hash large files?
Yes, but bigger files take longer. Keep the tab open until Hashly completes the calculation.
Image idea for your hero (alt text ready)
A minimalist Hashly panel with a selector for MD5, SHA-1, and SHA-256, a text/file input labeled “Enter text or upload file,” a bold “Generate” button, and a results line showing “SHA-256:” followed by a long monospace value with a copy icon; a small note underneath reads “Use hashes to verify downloads,” conveying speed and trust.
Related tools to round out your toolkit
Shafy — dedicated SHA generator when you want only SHA-1/256/512
Bcryptor — salted password hashing for logins and sensitive credentials
Final takeaway
Hashly turns verification into an easy habit. With instant MD5, SHA-1, and SHA-256 outputs, you can track versions, confirm downloads, and keep projects aligned without adding friction. Standardize on SHA-256, label your values clearly, and place them where your audience will see them. A few seconds with Hashly can save hours of second-guessing later.
Contact
Missing something?
Feel free to request missing tools or give some feedback using our contact form.
Contact Us