04
Shafy — Generate SHA Hashes Instantly
Generate SHA hashes instantly with Shafy. Create SHA-1, SHA-256, and SHA-512 checksums to verify files, track versions, and keep data consistent. Slug: /tools/shafy
Shafy is a fast, no-fuss way to create SHA hashes on demand. Paste text or upload a file, pick the algorithm you want—SHA-1, SHA-256, or SHA-512—and Shafy returns a clean checksum ready to copy and store. If you need a simple method to confirm a download, track versions, or spot accidental changes, Shafy gives you trustworthy hashes in seconds.
What a Hash Is (Without the Jargon)
Think of a hash as a “fingerprint” for data. Feed the same content in and you’ll always get the same fingerprint out; change even a single character or pixel and the fingerprint changes completely. This makes hashes perfect for quick authenticity checks, version tracking, and catching copy-paste mistakes before they become bigger issues.
Why People Use SHA Hashes Every Day
Verify downloads and transfers so you know a file didn’t get corrupted along the way
Track versions of documents and assets without juggling long file names
Detect accidental edits when collaborating across tools and teammates
Label large files with short, consistent identifiers that are easy to compare
Automate content checks in publishing, documentation, and release notes
SHA-1 vs. SHA-256 vs. SHA-512 — Which Should You Choose?
SHA-256 is the modern, widely recommended default. It balances speed with robust collision resistance for everyday integrity checks.
SHA-512 is another strong option, useful when you prefer a longer digest for policy or compliance reasons.
SHA-1 is considered legacy for security-critical tasks because researchers have demonstrated collisions. It can still be acceptable for low-risk, non-adversarial uses (like rough deduplication), but prefer SHA-256 or SHA-512 whenever possible.
What Shafy Does Well
Instant hashes for text or files with no setup required
Clear output you can copy with one click and paste into docs or spreadsheets
Support for multiple algorithms so you can follow your team’s standards
Readable interface that fits right into quick checks, handoffs, and audits
Helpful notes so teammates pick the right algorithm for the job
How to Use Shafy in Under a Minute
Open Shafy and select the algorithm (SHA-256 is a great default)
Paste your text or upload a file you want to check
Click “Generate” and copy the result
Store the hash next to your file, ticket, or release note so everyone can verify later
Everyday Scenarios Where Shafy Saves Time
Content publishing: Add a hash next to downloadable assets (PDFs, ZIPs, datasets) so readers can confirm authenticity.
Design and media: Drop hashes into handoff notes to ensure the file that ships is the one that was approved.
Docs and knowledge bases: Include a checksum for each resource file so editors catch accidental overwrites.
Education and research: Attach hashes to datasets and lab resources to make peer review smoother.
Ops and IT: Keep a reference hash for configuration files to spot unintended changes after updates.
Simple Practices for Clean, Reliable Hashing
Write down which algorithm you used each time. “SHA-256:” followed by the value removes guesswork later.
Store the hash next to the asset—in the same folder, ticket, or readme—so verification is obvious.
When you update a file, refresh the hash immediately; stale hashes create confusion.
For public downloads, include a short note: “Match this value to confirm your file downloaded correctly.”
Use lowercase consistently for readability, and avoid line breaks in long hashes.
What Hashes Can and Can’t Do
Hashes are excellent for integrity (detecting changes). They are not passwords and not secrets. If you need to protect user credentials, use slow, salted password hashing such as bcrypt (see Bcryptor). If you need encryption (keeping contents hidden), use proper encryption tools. Shafy focuses on quick, dependable fingerprints—not secrecy.
Common Mistakes (and Better Habits)
Mixing algorithms in the same project makes verification harder. Standardize on SHA-256 unless you have a reason not to.
Comparing hashes by eye leads to errors. Copy and compare full strings rather than scanning.
Forgetting to update the hash after a minor edit defeats the purpose. Make it part of your save/publish routine.
Treating SHA-1 as “secure enough” for adversarial scenarios is risky. Prefer SHA-256 or SHA-512 for long-term confidence.
Light SEO Tips If You Publish Hashes on Your Site
Add a brief sentence before each checksum explaining its purpose (“Use this SHA-256 to verify your download”).
Place hashes close to their corresponding download buttons to reduce confusion.
Use descriptive file names (e.g., brand-guidelines-v3.pdf) and include the algorithm label before the value.
Provide alt text for any image that displays a hash so the purpose is clear for screen readers.
Link to a short “How to verify” note for users who haven’t done it before.
FAQs
Are SHA hashes reversible?
No. Hashes are one-way fingerprints.
Is SHA-1 still safe?
It’s considered weak for collision resistance. For anything that matters, choose SHA-256 or SHA-512.
Which algorithm should I use by default?
Use SHA-256 unless your policy specifically asks for SHA-512.
Can I use Shafy for passwords?
No. For passwords, use a slow, salted algorithm like bcrypt (our Bcryptor tool). Plain SHA is not suitable for password storage.
Why does my hash change after a minor edit?
That’s expected. Hashes are designed to change if the input changes—even a single character.
Can I hash large files?
Yes, but expect longer processing times for big assets. Keep the browser tab open until Shafy finishes.
Team Workflow Ideas That Stick
Add a “Checksum” line to your release note template with the algorithm name and value
Create a shared “Verification” checklist for downloads and documentation pages
Keep a simple “Hash history” text file alongside important assets to track changes over time
Teach new teammates to verify hashes before publishing or handing off files
Include the hash in tickets and pull requests so reviewers can confirm artifacts quickly
Accessibility and Responsible Use
Always pair hashes with short, human-readable context (“Verify your file with this SHA-256 value”).
Avoid presenting hashes solely as images; keep a copyable text version.
If your audience is unfamiliar with checksums, link to a short explainer on how to compare values.
Do not imply that a hash prevents copying or guarantees authorship; it only confirms that content hasn’t changed.
Hero Image Description (Alt-Text Idea)
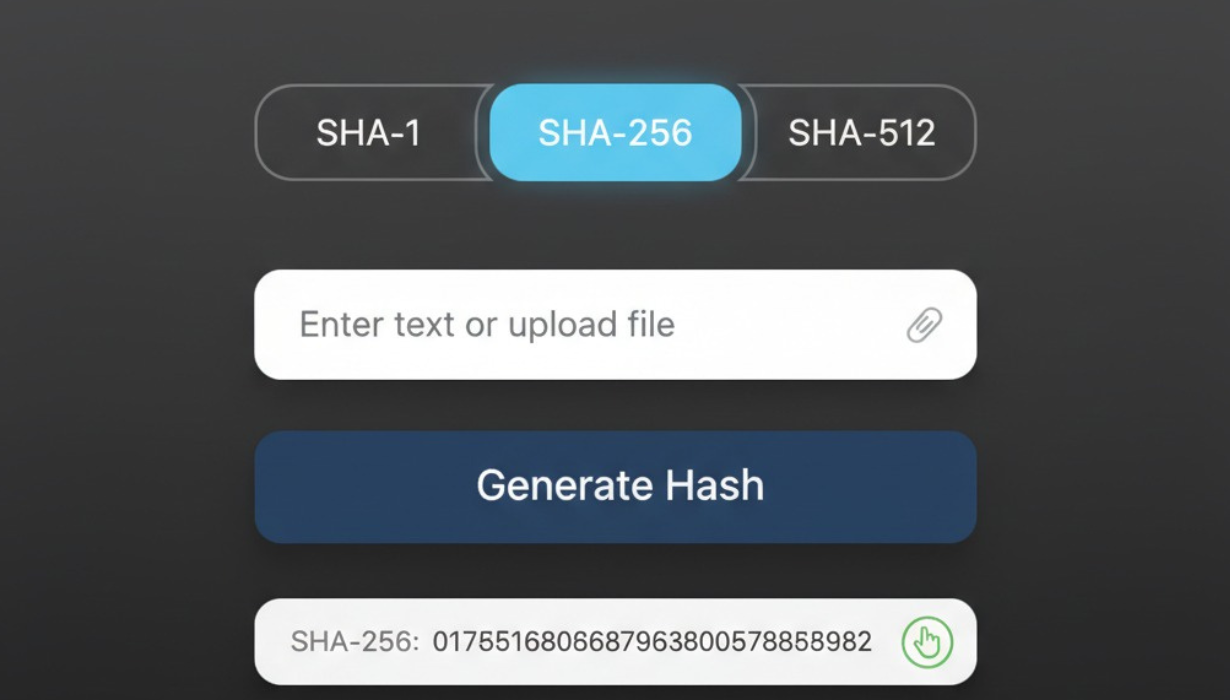
A clean Shafy interface on a soft slate gradient shows a simple selector with “SHA-1 / SHA-256 / SHA-512,” a text/file input labeled “Enter text or upload file,” a bold Generate Hash button, and a results panel with a clear “SHA-256:” label and a long value plus a one-click Copy icon; a small note reads “Use hashes to verify downloads,” and the layout feels minimal, fast, and trustworthy.
Final Takeaway
Shafy turns integrity checks into a quick habit you’ll actually keep. With instant SHA-1, SHA-256, and SHA-512 hashes, you can verify downloads, track versions, and keep projects consistent—without adding friction to your day. Use Shafy whenever you publish, share, or archive important files, and give your team an easy, reliable way to confirm that nothing changed along the way.
Contact
Missing something?
Feel free to request missing tools or give some feedback using our contact form.
Contact Us